Page 16 - The Bureau - Cyber Security Awareness e-book.indd
P. 16
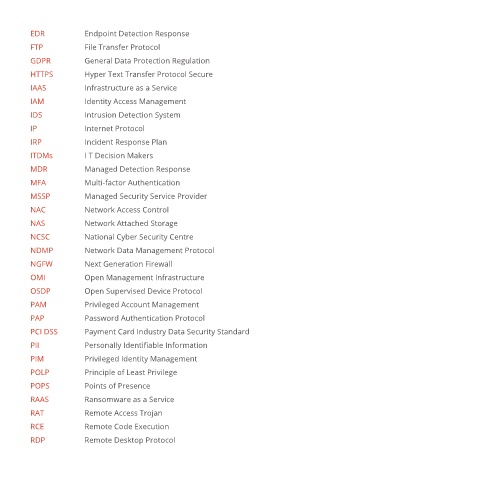
EDR Endpoint Detection Response
FTP File Transfer Protocol
GDPR General Data Protection Regulation
HTTPS Hyper Text Transfer Protocol Secure
IAAS Infrastructure as a Service
IAM Identity Access Management
IDS Intrusion Detection System
IP Internet Protocol
IRP Incident Response Plan
ITDMs I T Decision Makers
MDR Managed Detection Response
MFA Multi-factor Authentication
MSSP Managed Security Service Provider
NAC Network Access Control
NAS Network Attached Storage
NCSC National Cyber Security Centre
NDMP Network Data Management Protocol
NGFW Next Generation Firewall
OMI Open Management Infrastructure
OSDP Open Supervised Device Protocol
PAM Privileged Account Management
PAP Password Authentication Protocol
PCI DSS Payment Card Industry Data Security Standard
PII Personally Identifi able Information
PIM Privileged Identity Management
POLP Principle of Least Privilege
POPS Points of Presence
RAAS Ransomware as a Service
RAT Remote Access Trojan
RCE Remote Code Execution
RDP Remote Desktop Protocol